Data Governance
Data governance (DG) is the process of managing the availability, usability, integrity and security of the data in enterprise systems, based on internal data standards and policies that also control data usage. Effective data governance ensures that data is consistent and trustworthy and doesn't get misused. It's increasingly critical as organizations face new data privacy regulations and rely more and more on data analytics to help optimize operations and drive business decision-making.
Ethical Principles around Data
- Autonomy - The right to control your data, possibly via surrogates
- Informed consent - You should explicitly appove use of your data based on understanding
- Beneficence - People using your data should do it for your benefit
- Non-maleficence - Do no harm
Data Lineage
Cross Reference Tables
Cross-reference tables, sometimes referred to as XREF tables, are used for tracking the lineage of data, which systems and which records from those systems contributed to consolidated records, and also for tracking versions of data.
ODPi
ODPi creates open source standards to help you use and understand data across all platforms.
https://searchdatamanagement.techtarget.com/definition/data-governance
https://en.wikipedia.org/wiki/Data_governance
https://www.oreilly.com/content/data-governance-and-the-death-of-schema-on-read
Data governance frameworks
- DGI - Data Governance Institute
- DAMA DMBOK - Data Management Body of Knowledge (DMBOK)
- McKinsey
- Eckerson
- PwC
- Deloitte
- Control Objectives for Information and Related Technology (COBIT)
- SAS Data Governance Framework
- BCG Data Governance Framework
Data Governance Framework: Guide, Examples, Template
Top Data Governance Frameworks in 2024
Cheat Sheet
What is Sensitive Data?
Personally Identifiable Information (PII), Protected health information (PHI), intellectual property, financial information, education and legal records are all sensitive data.
Most countries have laws and regulations that require the protection of sensitive data. For example, the General Data Protection Regulation (GDPR) in the European Union sets stringent rules for data protection and privacy. Non-compliance with such regulations can result in hefty fines, legal actions, and sanctions against the violating entity.
When we design systems, we need to design for data protection.
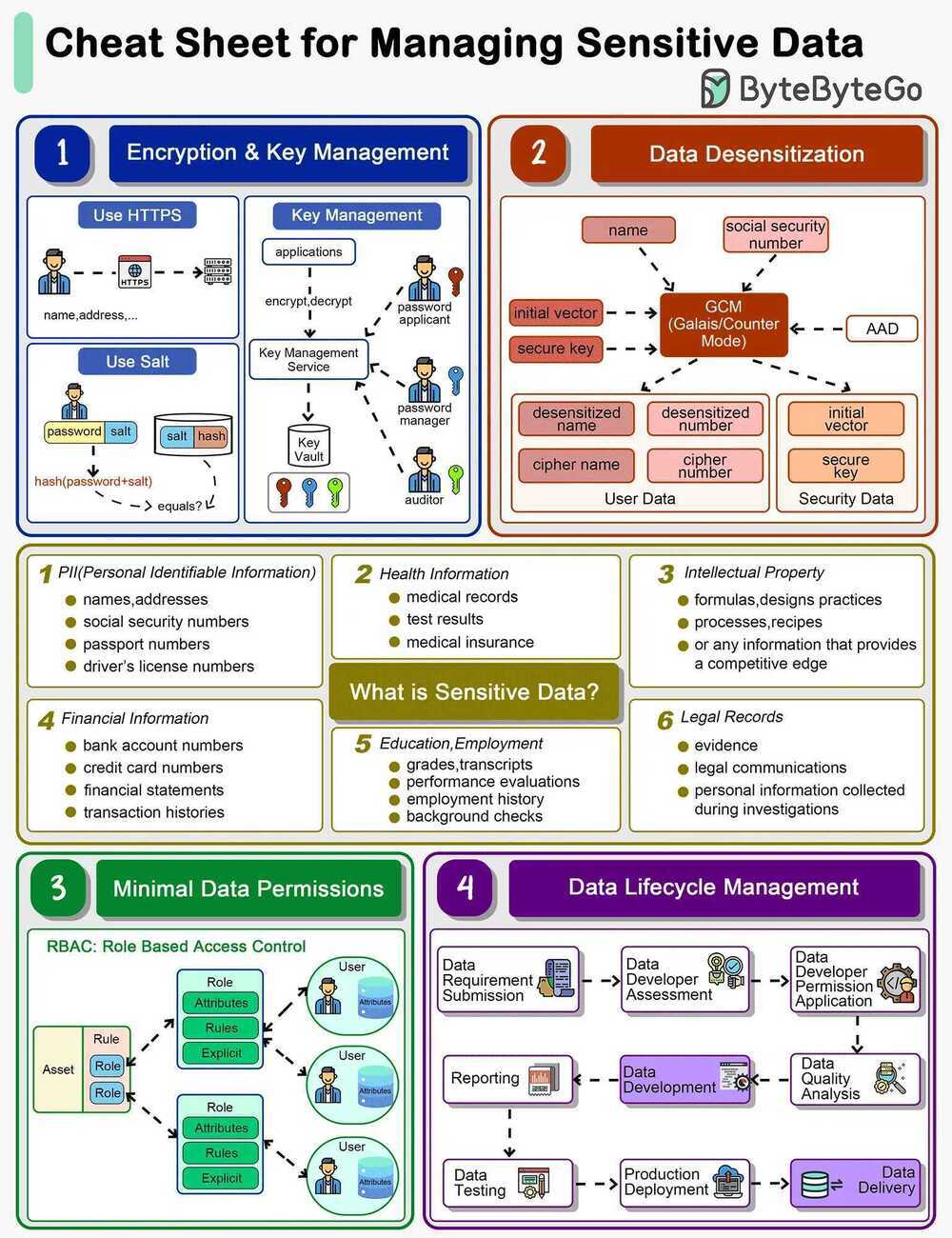
Encryption & Key Management
The data transmission needs to be encrypted using SSL. Passwords shouldn’t be stored in plain text.
For key storage, we design different roles including password applicant, password manager and auditor, all holding one piece of the key. We will need all three keys to open a lock.
Data Desensitization
Data desensitization, also known as data anonymization or data sanitization, refers to the process of removing or modifying personal information from a dataset so that individuals cannot be readily identified. This practice is crucial in protecting individuals' privacy and ensuring compliance with data protection laws and regulations. Data desensitization is often used when sharing data externally, such as for research or statistical analysis, or even internally within an organization, to limit access to sensitive information. Algorithms like GCM store cipher data and keys separately so that hackers are not able to decipher the user data.
Minimal Data Permissions
To protect sensitive data, we should grant minimal permissions to the users. Often we design Role-Based Access Control (RBAC) to restrict access to authorized users based on their roles within an organization. It is a widely used access control mechanism that simplifies the management of user permissions, ensuring that users have access to only the information and resources necessary for their roles.
Data Lifecycle Management
When we develop data products like reports or data feeds, we need to design a process to maintain data quality. Data developers should be granted with necessary permissions during development. After the data is online, they should be revoked from the data access.
Tools
Data Hub
The No. 1 open source metadata platform
Data Discovery and Lineage for Big Data Ecosystem
DataHub is a modern data catalog designed to streamline metadata management, data discovery, and data governance. It enables users to efficiently explore and understand their data, track data lineage, profile datasets, and establish data contracts. This extensible metadata management platform is built for developers to tame the complexity of their rapidly evolving data ecosystems and for data practitioners to leverage the total value of data within their organization.
DataHub: A generalized metadata search & discovery tool
DataHub Quickstart Guide | DataHub
docker-compose-without-neo4j-m1.quickstart.yml
GitHub - datahub-project/datahub: The Metadata Platform for your Data and AI Stack - 10.5k stars
# use python 3.11
python3 -m pip install --upgrade pip wheel setuptools
python3 -m pip install --upgrade acryl-datahub
datahub version
datahub docker quickstart
# http://localhost:9002
username: datahub
password: datahub
# ingest sample data
datahub docker ingest-sample-data
source:
type: bigquery
config:
project_id: your-gcp-project-id
credentials:
# If using a service account key file
filename: /path/to/service_account.json
include_tables: true
include_views: true
include_usage_stats: true
usage_stats:
top_n_queries: 25
sink:
type: datahub-rest
config:
server: http://localhost:8080
# datahub ingest -c ingestion/bigquery.yml
DataHub vs Apache Atlas
Both Apache Atlas and DataHub are open-source data catalog platforms designed to manage metadata, but they differ in their architecture, focus, and features.
- Apache Atlas, originally developed for the Hadoop ecosystem, emphasizes traditional governance with a strong integration within Hadoop.
- DataHub, on the other hand, takes a schema-first, real-time, and stream-based approach, focusing on comprehensive metadata management and governance.
Others
- Unified governance for data and AI | Collibra
- Talend
- Informatica
- Apache Atlas
- The Data Catalog Platform | data.world
- GCP DataPlex
- Microsoft Purview Data Governance | Microsoft Security